As technology advances, the line between efficiency and privacy violation becomes increasingly blurred. The recent case of Kmart Australia proves this — the retail giant was sanctioned by the country’s privacy regulator for collecting facial data from customers without consent.What…

Technology Isn’t Enough: Building Digital Trust in the Modern Business Era
Modern Business : Beyond Innovation — Businesses Need Trust to Thrive In an age where digital transformation defines competitiveness, many companies focus solely on adopting cutting-edge technologies, streamlining payment systems, and automating workflows. Yet one crucial element is often overlooked:…

Data Breach Response and Digital Trust: Essential Steps to Take After a Data Breach
A data breach is one of the most critical cybersecurity incidents an organization can face in the digital era. As businesses increasingly rely on digital systems to store personal data, customer records, and sensitive documents, the risk of unauthorized access…

Data Misappropriation Alleged: Tailor Haunted by Rp 2.8 Billion Tax Bill
A tailor in Pekalongan unexpectedly received a staggering tax bill of Rp 2.8 billion. The Directorate General of Taxes (DGT) firmly denies ever issuing such a demand to the individual concerned. The case is suspected to originate from data misappropriation…

Rising Loan Defaults in Online Lending: OJK Warns of Major Risks to Data Security & Financial Reputation
The phenomenon of widespread loan defaults (galbay) in online lending is increasingly prevalent across regions in Indonesia. The Financial Services Authority (OJK) cautions that these actions not only result in legal issues but also severely impact credit scores, financial reputations,…
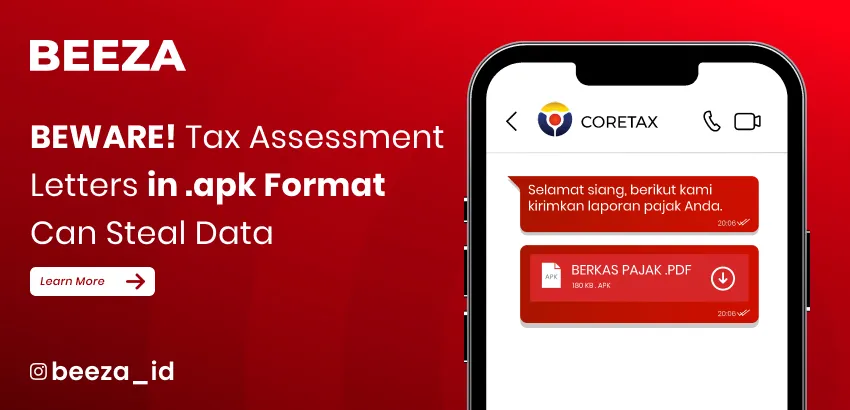
Beware of Fake Tax Certificates (SKP) in .apk Format: A New Scam Targeting Your Data
Digital fraud is becoming increasingly sophisticated. Recently, fake Tax Certificates (Surat Ketetapan Pajak or SKP) have been circulated in the form of .apk files. While they appear official at first glance, these files are actually malicious applications containing malware that…

Pros and Cons of Payment ID: Convenient for Transactions, But Is Your Data Safe?
Payment ID offers tremendous convenience in digital transactions — fast, practical, and simplifying payment records. However, behind this ease lie risks that cannot be ignored: data breaches, potential fraud, and digital identity misuse. This article explores the advantages and disadvantages…

Being Smart Isn’t Enough: Why Being a Responsible Digital Citizen Matters More Than Ever
In today’s hyper-connected world, being tech-savvy alone isn’t enough. We’re also expected to act with ethics, empathy, and responsibility as digital citizens. Let’s learn how to not just be smart online—but also wise and responsible. The Digital World Is No…

No Need for a Big IT Team — UMKM Can Use Beeza Too
1. Introduction: UMKM Face Digital Challenges Too When people talk about digital transformation, it’s usually associated with large enterprises or tech startups. But the reality is, Small and Medium Enterprises are just as much in need of going digital —…

Same Face, But Not the Same Person! As Deepfakes Get Smarter, Businesses Need eKYC That’s Fast and Secure
1. Introduction: Data is an Asset, Not a Burden Recent studies show that 60% of SMEs still overlook the importance of data protection. Many businesses still view cybersecurity as a “cost” rather than an investment. In today’s digital-first environment, data…
